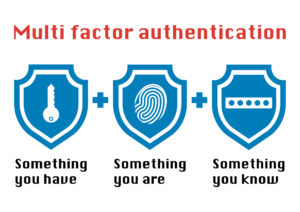
Multi-Factor Authentication Basics and How MFA Can Be Hacked
Identity theft is one of the main ways in which cyber-criminals can profit from hacking other people. Once you take on someone else’s identity, you

Identity theft is one of the main ways in which cyber-criminals can profit from hacking other people. Once you take on someone else’s identity, you

It always pays to know your enemy. More specifically, it pays to understand the methods of your enemies. To that end, we are going to

There are very few cyber-attacks that can equal ransomware in terms of effectiveness and safety. From the hacker’s perspective, they can use this kind of

Everyone needs to pay a certain amount of attention to their cybersecurity. You don’t have to be a business or a large organization, as private

When you are running a large-scale network with a lot of users, it becomes necessary to coordinate that network from a central location. Such a

The cloud has become an essential tool for many individuals and organizations. While it may not be necessary for everyone, it certainly does offer a

Not everyone needs to be a cybersecurity expert. Indeed, it takes a lot of studying to become proficient in that field. However, in an age

The use of cloud computing has grown to immense proportions in recent years. Many people have heralded the rise of the cloud as the next

In IT terms, an endpoint is any device that is used to access the network. This obviously includes desktops, laptops, and all mobile devices with

It seems that every network security precaution has at least one flaw. In fact, it is almost hard to imagine a cybersecurity model that doesn’t